DHCP
DHCP is a protocol helping assigning clients IP addresses in a Local Area Network (LAN). DHCP consists of 4 steps: DHCP discover, DHCP offer, DHCP request and DHCP ACK.
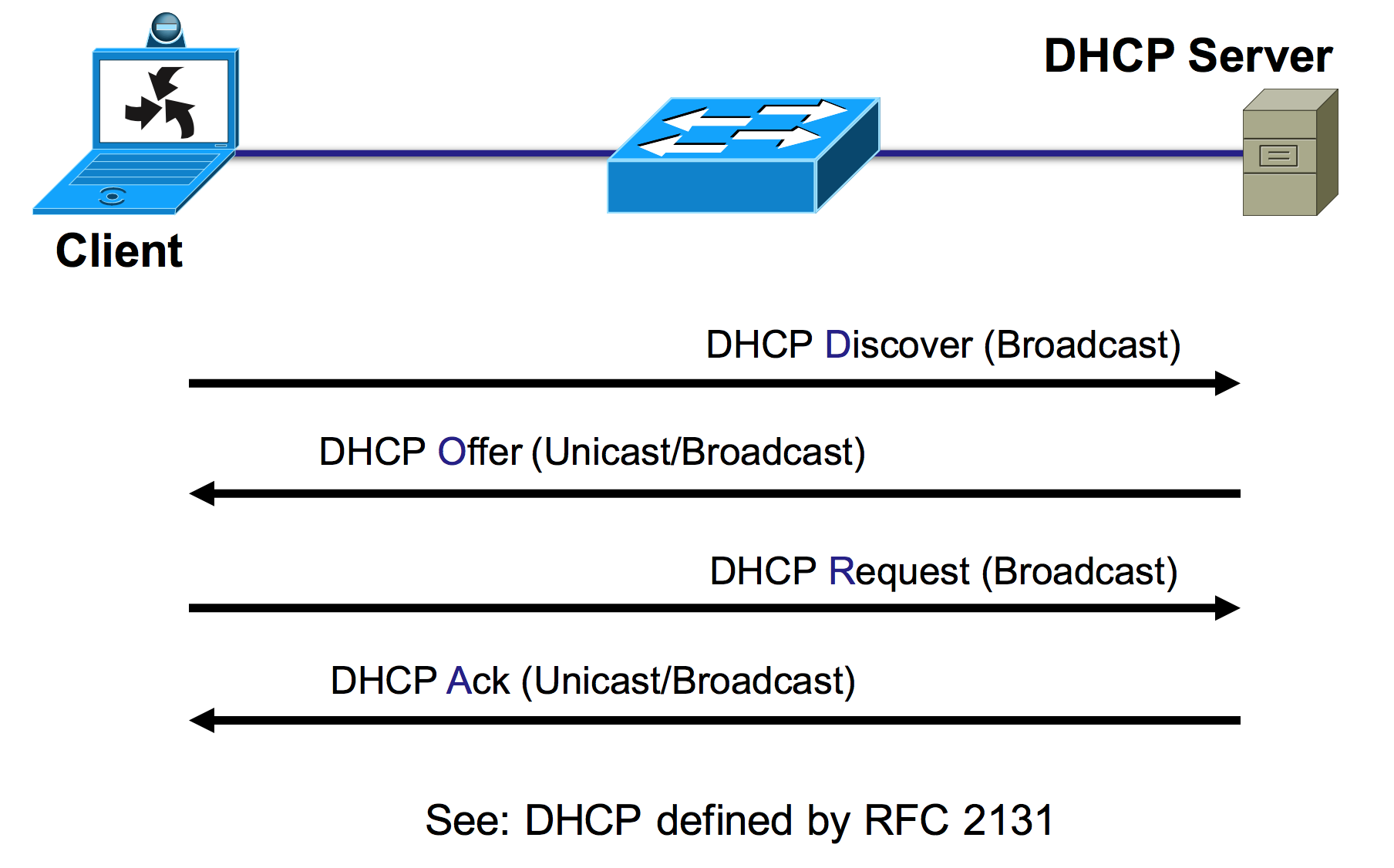
DHCP discover is like client broadcasting in LAN finding a DHCP server (often located at the router) who can give it an IP address. DHCP offer is the server offering a possible IP, while DHCP request is the client broadcasting to all other clients and the server that it is going to take that IP. The last step often differs in different situations, ACK stands for a success DHCP process, while NAK means the required IP is already taken by someone else.
However, this process is quite insecure, since we can establish a fake DHCP server since client use broadcast to find servers. Besides, we can also use different hardware addresses (MAC addresses. DHCP servers often store IP-to-MAC relationship) to ask for a lot of different IP addresses so that other clients can’t get an IP to get access to Internet, which is called DHCP starvation, kind of network attack.
In this article, we will focus on attack with DHCP request, which is the 3rd step. After we send DHCP requests, the server will assign requested IP to us, which is very helpful when we want to attack certain range of IP addresses. Attacking with DHCP discovery is also possible.
Scripts
We use ScaPy to help us practice DHCP starvation. ScaPy is a python library with networking and security features.
We establish a class called DHCPStarvation, which maintains two lists, one for MAC addresses and one for IP addresses. We need to store MAC addresses since we don’t want to send duplicate requests with the same MAC addresses (this won’t work because server has cache, as mentioned). We store IP addresses so that we can learn which IP addresses we have occupied to measure whether we succeed on certain scope.
|
|
The method handle_dhcp is how we handle DHCP ACK packets. we first check whether the DHCP packet is an ACK packet and then mark the destination IP address (which is the address assigned to us) as successfully occupied.
|
|
The class’s start() method includes two parts. One is using a thread to keep listening DHCP packets. The other one keep starting the starve method until all targeted IPs are registered.
|
|
The starve method send DHCP requests for certain IP in a loop. Everytime we try to generate a new MAC address and check whether current IP is already registered. We also use sleep to avoid congesting the link with DHCP, which will clearly decrease the efficiency of our attack.
|
|
Conclusion
As we can see, DHCP itself is a very fragile protocol which can be easily attacked and network disability can be easily caused. To avoid such attack, we can set limit for IP assigning on certain ports. Also we can try to identify abnormal DHCP discoveries or requests to react quickly to possible attack.