ARP is an essential protocol in today’s network which establish a connection between link layer and network layer. We all know that web address can be translated into IP address with DNS. But how can we know the hardware address of a certain IP address so that we can form the Ethernet header of a packet? ARP is our answer.
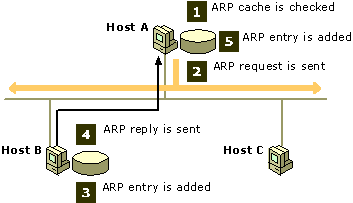
From the upper image we can understand how ARP works. Basically it’s about asking “Which MAC address has this IP address?” and answering “I’m occupying this IP address with this MAC address.” so that each host can construct a mapping between IP addresses and MAC addresses. The image shows the situation in a Local Area Network (LAN). If the requested IP is not in the same LAN, the router will answer the ARP request with its own MAC address.
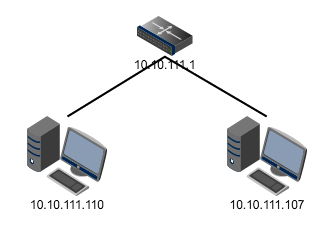
However, ARP can also be easily spoofed by ARP request. As we can see, a host will add information from received ARP into its entries at the 3rd step. Assuming we have a network as following, if the 107 client use ARP request to tell 110 that it’s 10.10.111.1 (which is IP of router) and tell router that it’s 10.10.111.110, the 107 host will successfully play as a LAN proxy between router and another host and be able to see all traffic if not encrypted. Damage of such a situation can be used by tools like SSLStrip. It mainly talks about partially secure web page transferred through HTTP can be depreciated and HTTPS links (majorly used for login) can be downgraded to HTTP (which makes username and password can be seen). What’s comforting is that most major websites are using HTTPS for the whole web page nowadays.
The following are the code of such a gratuitous ARP spoofing.
|
|